User Guide - Object Details
The Object Details guide provides additional specific information about threat intelligence objects and their relationships. It covers:
Options or edge cases that are specific to working with particular threat intelligence objects.
Detailed information on what nodes are displayed in the vertex-threat-intel Workflow, how the objects are “linked” or related to each other, and how the objects may be searched, where relevant. The Workflow is designed to simplify analysis tasks by masking many of these details. We include this information here for users who may be interested in how information in the Workflow relates to “raw” information in the Research Tool.
Tip
Refer to the User Guide - Threat Intel Model for general information about threat intelligence objects and their intended use.
Like the User Guide - Threat Intel Model, this guide is organized according to the types of objects displayed in the Workflow:
Note
The vertex-threat-intel Power-Up and associated Workflow are still a beta release and subject to change. This section will be revised as the Power-Up’s key features are finalized.
Threats
Threat Clusters
Threat clusters are represented by risk:threat nodes.
Selection Panel
In the Selection Panel, the THREAT CLUSTERS tab:
Displays: all
risk:threatnodes in your View.Searches:
The
risk:threat:nameproperty (“attributed to” column).The
risk:threat:namesproperty (not displayed in the Selection Panel but included in search).The
risk:threat:reportername ( “reporter” column).
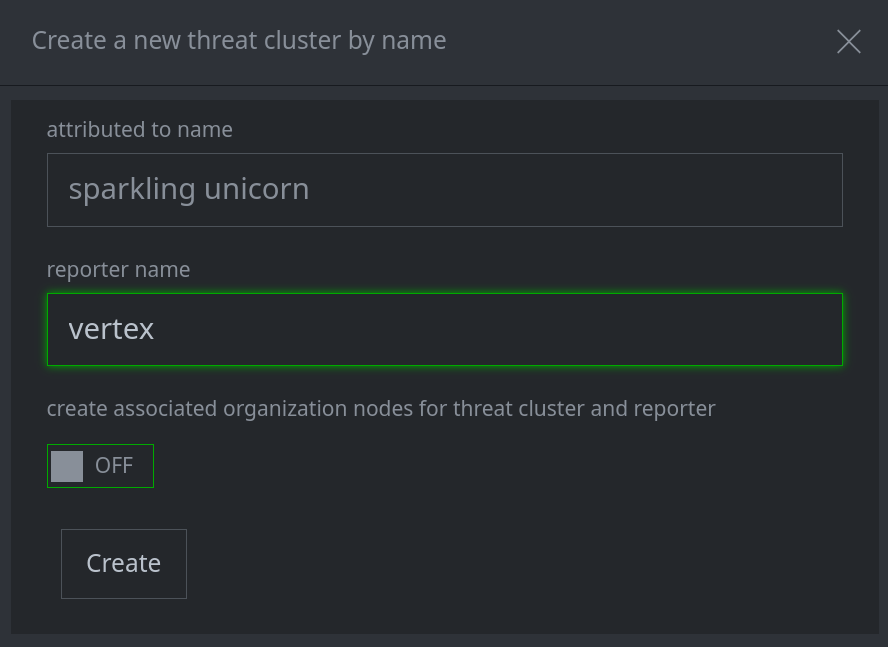
Creating a Threat Cluster:
When creating a new threat cluster, you have the option to:
Link the threat cluster to a threat group node (
ou:org) whose names include the threat cluster name (or create an organization node, if one does not exist). This will set therisk:threat:orgproperty.Link the threat cluster to a reporter organization node whose names include the reporter name (or create an organization node for the reporter, if one does not exist). This will set the
risk:threat:reporter:orgproperty.
Set the toggle switch to ON to perform both of these actions:
Tip
Currently, you must set both properties, or neither property. If you leave the toggle OFF, you can choose to set each property individually later when you Run Consistency Checks.
Profile Panel
In the Profile Panel, DETAILS tab, the following additional options are available:
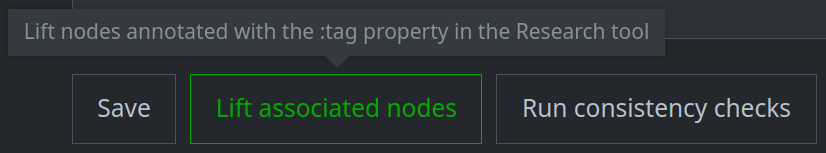
Lift associated nodes:
Click the lift associated nodes button to display all nodes tagged with the threat cluster tag in the Research Tool:
In the Profile Panel, the following links are created through the specified tabs:
TTPS > TOOLS | TECHNIQUES | VULNERABILITIES: Links nodes with a “uses” light edge:
risk:threat -(uses)> risk:tool:softwarerisk:threat -(uses)> ou:techniquerisk:threat -(uses)> risk:vuln
ACTIVITY > ALERTS | ATTACKS | COMPROMISES | CAMPAIGNS:
The activity is attributed to the threat cluster by tagging the activity node with the threat cluster’s
risk:threat:tagvalue.
TARGETING > COUNTRIES | INDUSTRIES: Links nodes with a “targets” light edge:
risk:threat -(targets)> pol:countryrisk:threat -(targets)> ou:industry
TARGETING > GOALS:
The
ou:goalis added to therisk:threat:goalsarray property.
IN THE NEWS: Links nodes with a “refs” light edge:
media:news -(refs)> risk:threat
Threat Groups
Threat groups are represented by ou:org nodes.
Selection Panel
In the Selection Panel, the THREAT GROUPS tab:
Displays a subset of
ou:orgnodes in your View:Organization nodes that are explicitly linked to a threat cluster via the cluster’s
risk:threat:orgproperty.Organizations whose
:_vertex:threatintel:isthreatproperty is set to True.
Searches the threat group name:
ou:org:name(“name” column).ou:org:names(not displayed in the Selection Panel but included in search).
Profile Panel
In the Profile Panel, the following links are created through the specified tabs:
THREAT CLUSTERS
Links the specified threat cluster(s) to the group by setting the
risk:threat:orgproperty of the threat cluster to the value (guid) of the threat group’sou:orgnode.
TTPS > TOOLS | TECHNIQUES | VULNERABILITIES: Links nodes with a “uses” light edge:
ou:org -(uses)> risk:tool:softwareou:org -(uses)> ou:techniqueou:org -(uses)> risk:vuln
ACTIVITY > ATTACKS | COMPROMISES:
Sets the
risk:attack:attackerorrisk:compromise:attackerproperty to the value (guid) of the threat group’s primary contact (ou:org:hqproperty).
ACTIVITY > CAMPAIGNS:
Sets the
ou:campaign:orgproperty to the value (guid) of the threat group’sou:orgnode.
TARGETING > COUNTRIES | INDUSTRIES: Links nodes with a “targets” light edge:
ou:org -(targets)> pol:countryou:org -(targets)> ou:industry
TARGETING > GOALS:
The
ou:goalis added to theou:org:goalsarray property.
IN THE NEWS: Links nodes with a “refs” light edge:
media:news -(refs)> ou:org
TTPs
Tools
Tools are represented by risk:tool:software nodes.
Selection Panel
In the Selection Panel, the TOOLS tab:
Displays: all
risk:tool:softwarenodes in your View.Searches:
The
risk:tool:software:soft:nameproperty (“name” column).The
risk:tool:software:soft:namesproperty (not displayed in the Selection Panel but included in search).The
risk:tool:software:reportername ( “reporter” column).
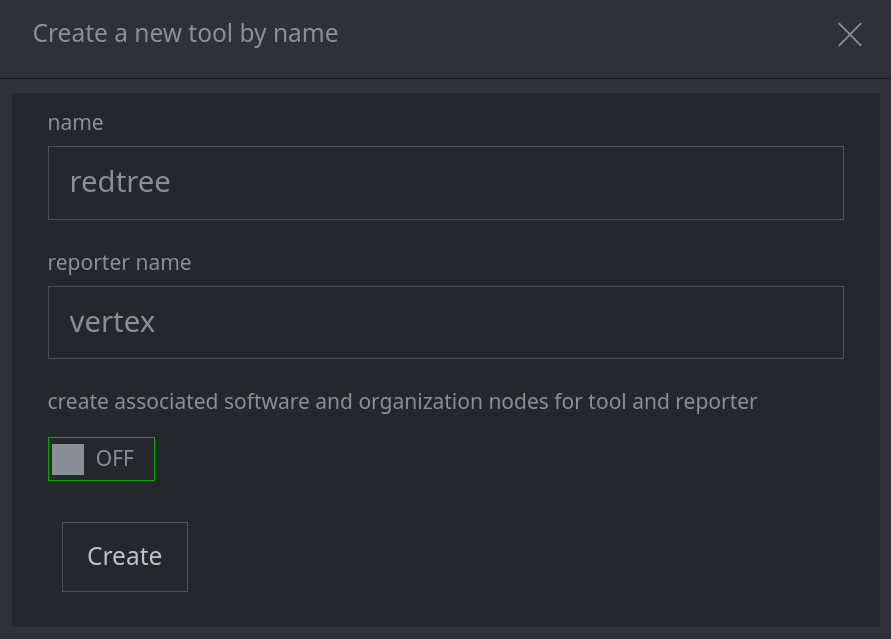
Creating a Tool:
When creating a new tool, you have the option to:
Link the tool to a software node (
it:prod:soft) whose names include the tool name (or create a software node, if one does not exist). This will set therisk:tool:software:softproperty.Link the tool to a reporter organization node whose names include the reporter name (or create an organization node for the reporter, if one does not exist). This will set the
risk:tool:software:reporter:orgproperty.
Set the toggle switch to ON to perform both of these actions:
Tip
Currently, you must set both properties, or neither property. If you leave the toggle OFF, you can choose to set each property individually later when you Run Consistency Checks.
Profile Panel
In the Profile Panel, DETAILS tab, the following additional options are available:
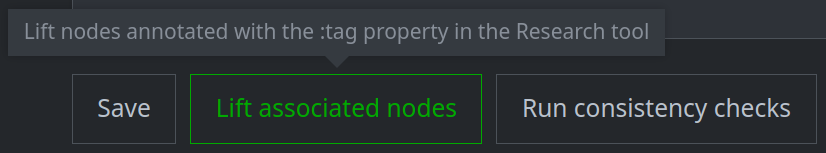
Lift associated nodes:
Click the lift associated nodes button to display all nodes tagged with the tool tag in the Research Tool:
In the Profile Panel, the following links are created through the specified tabs:
TECHNIQUES: Links nodes with a “uses” light edge:
risk:tool:software -(uses)> ou:technique
VULNERABILITIES: Links nodes with a “uses” light edge:
risk:tool:software -(uses)> risk:vuln
THREAT CLUSTERS: Links nodes with a “uses” light edge:
risk:threat -(uses)> risk:tool:software
THREAT GROUPS: Links nodes with a “uses” light edge:
ou:org -(uses)> risk:tool:software
IN THE NEWS: Links nodes with a “refs” light edge:
media:news -(refs)> risk:tool:software
Software
Software is represented by it:prod:soft nodes.
Selection Panel
In the Selection Panel, the SOFTWARE tab:
Displays a subset of
it:prod:softnodes in your View:Software nodes that are explicitly linked to a tool via the tool’s
risk:tool:software:softproperty.Software whose
:_vertex:threatintel:istoolproperty is set to True.
Searches the software name:
it:prod:soft:name(“name” column).it:prod:soft:names(not displayed in the Selection Panel but included in search).
Profile Panel
In the Profile Panel, the following links are created through the specified tabs:
TOOLS
Links the specified tool(s) to the software by setting the
risk:tool:software:softproperty of the tool to the value (guid) of the software’sit:prod:softnode.
VULNERABILITIES: Links nodes with a “uses” light edge:
it:prod:soft -(uses)> risk:vuln
IN THE NEWS: Links nodes with a “refs” light edge:
media:news -(refs)> it:prod:soft
Techniques
Techniques are represented by ou:technique nodes.
Selection Panel
In the Selection Panel, the TECHNIQUES tab:
Displays all
ou:techniquenodes in your View.Searches the technique name:
ou:technique:name(“name” column).
Tip
Technique names are normalized to lowercase. Case is ignored when searching for a technique name.
Profile Panel
In the Profile Panel, the following links are created through the specified tabs:
TOOLS: Links nodes with a “uses” light edge:
risk:tool:software -(uses)> ou:technique
VULNERABILITIES: Links nodes with a “uses” light edge:
risk:vuln -(uses)> ou:technique
THREAT CLUSTERS: Links nodes with a “uses” light edge:
risk:threat -(uses)> ou:technique
THREAT GROUPS: Links nodes with a “uses” light edge:
ou:org -(uses)> ou:technique
IN THE NEWS: Links nodes with a “refs” light edge:
media:news -(refs)> ou:technique
Vulnerabilities
Vulnerabilities are represented by risk:vuln nodes.
Selection Panel
In the Selection Panel, the VULNERABILITIES tab:
Displays all
risk:vulnnodes in your View.Searches the vulnerability name:
risk:vuln:name(“name” column).
Tip
Vulnerability names are case-sensitive. Prefix searches must match exactly with respect to case. Token searches (available if the synapse-search Advanced Power-Up is installed) are case-insensitive, as tokens are normalized to lowercase when they are indexed.
Profile Panel
In the Profile Panel, the following links are created through the specified tabs:
TOOLS: Links nodes with a “uses” light edge:
risk:tool:software -(uses)> risk:vuln
SOFTWARE: Links nodes with a “uses” light edge:
it:prod:soft -(uses)> risk:vuln
TECHNIQUES: Links nodes with a “uses” light edge:
risk:vuln -(uses)> ou:technique
THREAT CLUSTERS: Links nodes with a “uses” light edge:
risk:threat -(uses)> risk:vuln
THREAT GROUPS: Links nodes with a “uses” light edge:
ou:org -(uses)> risk:vuln
IN THE NEWS: Links nodes with a “refs” light edge:
media:news -(refs)> risk:vuln
Activities
Alerts
Alerts are represented by risk:alert nodes.
Selection Panel
In the Selection Panel, the ALERTS tab:
Displays all
risk:alertnodes in your View.Searches the alert name:
risk:alert:name(“name” column).
Tip
Alert names are case-sensitive. Prefix searches must match exactly with respect to case. Token searches (available if the synapse-search Advanced Power-Up is installed) are case-insensitive, as tokens are normalized to lowercase when they are indexed.
Profile Panel
In the Profile Panel, the following links are created through the specified tabs:
THREAT CLUSTERS:
Attributes an alert to a threat cluster (or clusters) by tagging the
risk:alertwith the threat cluster’s associated tag (risk:threat:tag).
Attacks
Attacks are represented by risk:attack nodes.
Selection Panel
In the Selection Panel, the ATTACKS tab:
Displays all
risk:attacknodes in your View.Searches the attack name:
risk:attack:name(“name” column).
Tip
Attack names are case-sensitive. Prefix searches must match exactly with respect to case. Token searches (available if the synapse-search Advanced Power-Up is installed) are case-insensitive, as tokens are normalized to lowercase when they are indexed.
Profile Panel
In the Profile Panel, the following links are created through the specified tabs:
USED TECHNIQUES: Links nodes with a “uses” light edge:
risk:attack -(uses)> ou:technique
TARGET INDUSTRIES: Links nodes with a “targets” light edge:
risk:attack -(targets)> ou:industry
TARGET ORGANIZATIONS: Links nodes with a “targets” light edge:
risk:attack -(targets)> ou:org
IN THE NEWS: Links nodes with a “refs” light edge:
media:news -(refs)> risk:attack
Note
To attribute an attack to a threat cluster, use the Selection Panel to right-click the attack. Select add tags to apply the associated threat cluster tag, or use the THREAT CLUSTERS > ACTIVITY tab to attribute the activity.
To attribute an attack to a threat group, use the DETAILS tab in the Profile Panel to set the “attacker name” property to the name of the threat group, or use the THREAT GROUPS > ACTIVITY tab to attribute the activity.
Compromises
Compromises are represented by risk:compromise nodes.
Selection Panel
In the Selection Panel, the COMPROMISES tab:
Displays all
risk:compromisenodes in your View.Searches the compromise name:
risk:compromise:name(“name” column).
Tip
Compromise names are normalized to lowercase. Case is ignored when searching for a compromise name.
Profile Panel
In the Profile Panel, the following links are created through the specified tabs:
TARGET INDUSTRIES: Links nodes with a “targets” light edge:
risk:compromise -(targets)> ou:industry
ATTACKS:
Associates the attack(s) with the compromise by setting the attack’s
risk:attack:compromiseproperty to the value (guid) of the compromise node.
THREAT CLUSTERS:
Attributes a compromise to a threat cluster (or clusters) by tagging the
risk:compromisewith the threat cluster’s associated tag (risk:threat:tag).
Tip
To attribute a compromise to a threat group, use the DETAILS tab to set the “attacker” value to the name of the threat group, or use the THREAT GROUPS > ACTIVITY tab to attribute the activity.
IN THE NEWS: Links nodes with a “refs” light edge:
media:news -(refs)> risk:compromise
Campaigns
Campaigns are represented by ou:campaign nodes.
Selection Panel
In the Selection Panel, the CAMPAIGNS tab:
Displays all
ou:campaignnodes in your View.Searches the campaign name:
ou:campaign:name(“name” column).
Tip
Campaign names are case-sensitive. Prefix searches must match exactly with respect to case. Token searches (available if the synapse-search Advanced Power-Up is installed) are case-insensitive, as tokens are normalized to lowercase when they are indexed.
Profile Panel
In the Profile Panel, the following links are created through the specified tabs:
ATTACKS:
Associates the attack(s) with the campaign by setting the attack’s
risk:attack:campaignproperty to the value (guid) of the campaign node.
COMPROMISES:
Associates the compromise(s) with the campaign by setting the compromise’s
risk:compromise:campaignproperty to the value (guid) of the campaign node.
TECHNIQUES: Links nodes with a “uses” light edge:
ou:campaign -(uses)> ou:technique
GOALS:
The
ou:goalis added to theou:campaign:goalsarray property.
THREAT CLUSTERS:
Attributes a campaign to a threat cluster (or clusters) by tagging the
risk:campaignwith the threat cluster’s associated tag (risk:threat:tag).
Tip
To attribute a campaign to a threat group, use the THREAT GROUPS > ACTIVITY tab to attribute the activity.
IN THE NEWS: Links nodes with a “refs” light edge:
media:news -(refs)> ou:campaign
Targeting
Industries
Industries are represented by ou:industry nodes.
Selection Panel
In the Selection Panel, the INDUSTRIES tab:
Displays all
ou:industrynodes in your View.Searches the industry name:
ou:industry:name(“name” column).ou:industry:names(not displayed in the Selection Panel but included in search).
Tip
Industry names are normalized to lowercase. Case is ignored when searching for a industry name.
Profile Panel
In the Profile Panel, the following links are created through the specified tabs:
TARGETED BY THREAT GROUPS: Links nodes with a “targets” light edge:
ou:org -(targets)> ou:industry
TARGETED BY THREAT CLUSTERS: Links nodes with a “targets” light edge:
risk:threat -(targets)> ou:industry
IN THE NEWS: Links nodes with a “refs” light edge:
media:news -(refs)> ou:industry
Goals
Goals are represented by ou:goal nodes.
Selection Panel
In the Selection Panel, the GOALS tab:
Displays all
ou:goalnodes in your View.Searches the goal name:
ou:goal:name(“name” column).
Tip
Goal names are case-sensitive. Prefix searches must match exactly with respect to case. Token searches (available if the synapse-search Advanced Power-Up is installed) are case-insensitive, as tokens are normalized to lowercase when they are indexed.
Profile Panel
In the Profile Panel, the following links are created through the specified tabs:
CAMPAIGNS:
The
ou:goalis added to theou:campaign:goalsarray property.
THREAT GROUPS:
The
ou:goalis added to theou:org:goalsarray property.
THREAT CLUSTERS:
The
ou:goalis added to therisk:threat:goalsarray property.
IN THE NEWS: Links nodes with a “refs” light edge:
media:news -(refs)> ou:goal
Organizations
Organizations are represented by ou:org nodes.
Selection Panel
In the Selection Panel, the ORGANIZATIONS tab:
Displays all
ou:orgnodes in your View.Searches the organization name:
ou:org:name(“name” column).ou:org:names(not displayed in the Selection Panel but included in search).
Tip
Organization names are normalized to lowercase. Case is ignored when searching for an organization name.
Profile Panel
In the Profile Panel, the following links are created through the specified tabs:
INDUSTRIES:
The
ou:industryis added to theou:org:industriesarray property.
ACTIVITY > TARGETED BY ATTACKS: Links nodes with a “targets” light edge:
risk:attack -(targets)> ou:org
ACTIVITY > TARGETED BY COMPROMISES:
Sets the target property of the compromise (
risk:compromise:target) to the value (guid) of the organization’s primary contact (ou:org:hq).
IN THE NEWS: Links nodes with a “refs” light edge:
media:news -(refs)> ou:org